By: Shane Turner, D.B.A.
8 October 2024

Introduction
The increasing complexity and sophistication of cyber threats have necessitated a significant paradigm shift in cybersecurity practices across the globe. Among the strategies that have gained prominence is Zero Trust (ZT), an evolving cybersecurity framework built upon the foundational principle of “never trust, always verify.” As a critical strategy for securing information systems, the Department of Defense (DoD) has emerged as a major advocate of Zero Trust. This white paper provides an in-depth analysis of the core principles of Zero Trust, the key drivers behind its adoption, and the complexities involved in its implementation within the DoD.
Understanding Zero Trust
Zero Trust is not merely a technology but a philosophy that seeks to eliminate the implicit trust inherent in traditional perimeter-based security models. Unlike conventional approaches that assume entities within a network are trustworthy, Zero Trust is predicated on the idea that no user, device, or application can be inherently trusted. The Zero Trust model focuses on continuously verifying every individual and device attempting to access resources, regardless of whether they are located inside or outside the network perimeter. In a Zero Trust environment, organizations enforce granular security controls and adopt a defense-in-depth approach to provide comprehensive protection against evolving cyber threats.
The principles of Zero Trust can be summarized as follows:
- Continuous Verification: Every user, device, and application must be authenticated and authorized each time they request access to resources. Trust is established dynamically, based on factors such as behavior analytics, contextual information, and the nature of access requests. This dynamic approach ensures that trust is never static and is continuously re-evaluated to maintain security.
- Least-Privilege Access: A core tenet of Zero Trust is enforcing least-privilege access, ensuring that users are granted the minimum access required to perform their tasks. By restricting access rights, organizations can minimize potential attack vectors and significantly mitigate the risk of insider threats. This principle requires robust access management and precise policy enforcement to be effective.
- Microsegmentation: Zero Trust emphasizes the need to segment networks into smaller, isolated microsegments to limit the lateral movement of attackers. Each microsegment contains resources grouped based on sensitivity or risk level, with specific access controls and monitoring mechanisms applied to each segment. By restricting movement within the network, microsegmentation provides a powerful mechanism for containing breaches and minimizing damage.
- Assume Breach: The Zero Trust model operates on the assumption that breaches are inevitable. Instead of relying solely on prevention, Zero Trust focuses on preparedness, rapid containment, and swift response. By assuming a breach is always possible, organizations adopt a proactive approach, incorporating continuous monitoring, threat detection, and incident response readiness to effectively mitigate the impact of security incidents.
- Context-Based Security: Security decisions are based on contextual information, such as user location, device type, time of access, and the risk profile of the request. Contextual analysis enables the implementation of adaptive security policies that dynamically adjust based on the perceived level of risk, ensuring that appropriate verification and enforcement are applied in real time.
Drivers of Zero Trust Adoption in the DoD
The adoption of Zero Trust by the DoD is driven by the need to address an evolving threat landscape and enhance the protection of mission-critical data. Several key drivers have catalyzed this transformation, including:
- Increasing Cyber Threats: The DoD faces a wide range of sophisticated cyber threats, particularly from state-sponsored actors. Traditional security models have proven insufficient to combat advanced persistent threats (APTs) and the myriad tactics, techniques, and procedures (TTPs) employed by adversaries. Zero Trust is essential for defending against these increasingly complex threats.
- Erosion of the Network Perimeter: With the widespread adoption of cloud services, remote work, and mobile devices, the traditional concept of a network perimeter has become obsolete. The growing reliance on remote access and cloud-based collaboration tools has blurred the lines between internal and external networks, necessitating a security model that is not dependent on a fixed perimeter. Zero Trust addresses these challenges by treating every access request as untrusted, regardless of its origin.
- Compliance and Policy Mandates: Policy directives, such as Executive Order 14028 on Improving the Nation’s Cybersecurity, as well as guidelines from the National Institute of Standards and Technology (NIST), have underscored the need for adopting Zero Trust to protect federal information systems. The DoD, in alignment with these mandates, aims to lead the charge in embracing Zero Trust and setting a standard for other federal entities.
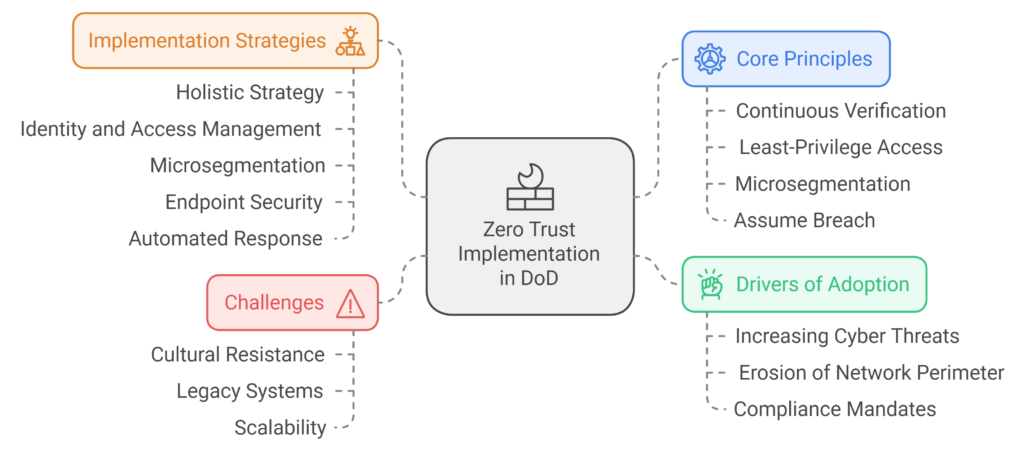
Implementation of Zero Trust by the DoD
The DoD’s approach to implementing Zero Trust is anchored in its Zero Trust Reference Architecture, which outlines best practices and a strategic roadmap for moving away from traditional perimeter-focused defense mechanisms. Key steps taken by the DoD to implement Zero Trust include:
- Adopting a Holistic Zero Trust Strategy: The DoD has developed a comprehensive Zero Trust Strategy and Roadmap to guide the department’s transition. This document prioritizes digital modernization and the consistent application of Zero Trust principles across the enterprise. The strategy involves collaboration among various stakeholders, including government agencies, contractors, and industry partners, to ensure a unified approach to Zero Trust implementation. Additionally, the strategy emphasizes awareness-building and training to ensure that personnel understand the principles and operational implications of Zero Trust.
- Identity and Access Management (IAM): The DoD’s identity and access management initiatives are central to its Zero Trust implementation. Continuous authentication is facilitated through multifactor authentication (MFA), endpoint trust evaluation, and context-aware access policies. The DoD is also enhancing privileged access management (PAM) to ensure that only authorized personnel can access critical systems. The use of identity federation and single sign-on (SSO) technologies further streamlines secure access across multiple domains while maintaining stringent identity verification requirements.
- Microsegmentation of Network Resources: Microsegmentation is employed by the DoD to segregate its network into distinct security zones, each with tailored access policies and monitoring protocols. These zones restrict communication pathways between resources, limiting an adversary’s ability to move laterally in the event of a breach. The continuous monitoring of each microsegment for abnormal activity further strengthens the DoD’s defense posture, ensuring that potential threats are contained within isolated network segments.
- Deploying Endpoint Security and Threat Intelligence: The DoD has prioritized ensuring that endpoints, including devices used by remote personnel, are secured and constantly monitored. The use of endpoint detection and response (EDR) systems, combined with AI-driven threat intelligence, helps identify and mitigate threats in real time. Endpoint security measures are extended to include mobile devices, which are subject to stringent security policies. The incorporation of machine learning and AI capabilities enhances proactive threat identification, providing an additional layer of security.
- Automated Response and Orchestration: Security automation plays a key role in the DoD’s Zero Trust implementation. The use of Security Orchestration, Automation, and Response (SOAR) tools enables rapid containment and response to cyber threats. Automation of routine security tasks, such as patch management and incident response, allows security personnel to focus on higher-level threats and analysis. By reducing the time between detection and response, the DoD can significantly minimize dwell time and mitigate the impact of cyber incidents.
- Secure Access to Classified and Mission-Critical Systems: The implementation of Zero Trust within the DoD also involves securing access to classified information and mission-critical systems. Technologies such as Secure Access Service Edge (SASE) and Software-Defined Perimeters (SDP) are leveraged to secure access consistently across environments. Data encryption, both at rest and in transit, is utilized to ensure the confidentiality of sensitive information. Additionally, role-based access control (RBAC) and attribute-based access control (ABAC) mechanisms are implemented to enforce strict policies governing access to classified systems.
Challenges in Implementing Zero Trust
Despite the significant advantages of Zero Trust, its implementation within the DoD is accompanied by several challenges. Key challenges include:
- Cultural and Organizational Resistance: The adoption of Zero Trust requires a fundamental cultural shift within the organization. Resistance to change, particularly in a large and hierarchical organization like the DoD, is a major obstacle. Strong leadership, effective communication, and comprehensive training are necessary to foster a culture that values cybersecurity resilience and to overcome the perception that Zero Trust increases complexity or reduces efficiency.
- Legacy Systems: Many of the systems used by the DoD are legacy infrastructures that were not designed to operate in a Zero Trust environment. Integrating these legacy systems into a modern Zero Trust architecture may require substantial modernization or replacement, both of which involve significant costs. Legacy systems that lack support for continuous authentication or microsegmentation must be prioritized for upgrades to ensure that the implementation of Zero Trust does not compromise operational readiness.
- Scalability: The DoD’s operations span multiple domains, including traditional IT systems, operational technology (OT), and battlefield systems. Scaling Zero Trust solutions across these domains is a complex technical challenge, as each domain has distinct requirements and constraints. The DoD must develop tailored Zero Trust solutions that meet the specific needs of each environment while maintaining interoperability and consistent security enforcement. Avoiding undue complexity that could impair mission effectiveness is also a key consideration in scaling Zero Trust.
The adoption of Zero Trust by the Department of Defense reflects an acknowledgment that traditional perimeter-based cybersecurity approaches are insufficient in the face of modern, sophisticated threats. The core principles of Zero Trust—continuous verification, least-privilege access, microsegmentation, and assuming breach—form a robust framework for defending against both external and internal threats. By implementing Zero Trust, the DoD is proactively working to strengthen its cybersecurity posture, even as it contends with the challenges of integrating legacy systems, addressing cultural resistance, and scaling across diverse environments. As cyber threats continue to evolve, the Zero Trust model will play an essential role in ensuring that the DoD remains resilient, adaptive, and capable of fulfilling its mission.
The path to Zero Trust is not a rapid transition but a profound change in how networks are secured and how security teams conceptualize trust. By adhering to key Zero Trust principles and addressing the inherent challenges, the DoD aims to fortify its cybersecurity defenses and set a precedent for other government agencies and private-sector organizations.
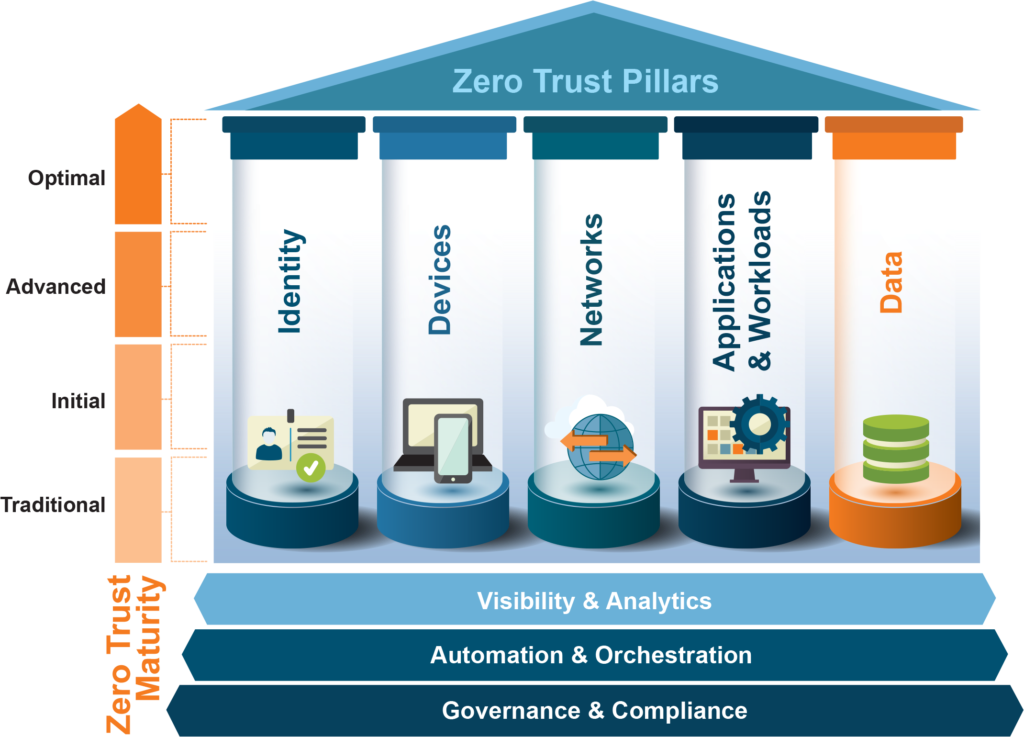
DoD Zero Trust Strategy
Other Information and Sources:
- Zero Trust Blog Series – Blog 1: Adopting a Zero Trust Mindset
- Zero Trust Blog Series – Blog 2: Architecting for Zero Trust
- Zero Trust Blog Series – Blog 3: Instrumenting for Zero Trust
- Zero Trust Blog Series – Blog 4: Operating for Zero Trust
Zero-Trust Cybersecurity fundamentally shifts the paradigm from traditional network security models, which often rely on a perimeter-based approach that assumes trust within the network. In contrast, Zero Trust operates on the principle of “never trust, always verify,” requiring continuous authentication and strict access controls regardless of the user’s location or device (Kumar, 2024) (Mythrayie & Sri, 2024). This model addresses the vulnerabilities of conventional security frameworks, particularly in dynamic IT environments and cloud services, by implementing components such as Policy Enforcement Points (PEP) and Identity and Access Management (IAM) (Lin et al., 2024). Furthermore, Zero Trust emphasizes micro-segmentation and least privilege access, which limits user permissions to only what is necessary, thereby reducing the attack surface (Kumar, 2024) (Gupta et al., 2024). The integration of advanced technologies, including quantum security measures, further enhances the robustness of Zero Trust architectures, making them more resilient against evolving cyber threats (Lin et al., 2024) (Pokhrel, 2024).